Equifax Breach: 8 Takeaways
After Equifax on Thursday warned that 143 million consumers' personal details may have been stolen by hackers, criticism of the consumer credit reporting agency - and data broker - has been swift.
Many security experts are asking how attackers were able to exploit the "website application vulnerability" cited by Equifax to steal so much personal information. Indeed, the breach may have exposed Social Security numbers for nearly half of all Americans.
On Friday, New York Attorney General Eric T. Schneiderman announced he has launched a formal investigation into the Equifax breach and has sent a letter to the company seeking additional information about the incident. Meanwhile, attorneys general in Connecticut, Illinois and Pennsylvania announced they plan to sent a joint letter requesting details from Equifax. Plus, the House Energy and Commerce Committee and Financial Services Committee announced plans to hold hearings to examine the massive data breach, according to The Hill.
Here are eight takeaways from the breach.
1. Breach Burns SSNs
Equifax says many of the 143 million breach victims had their names, Social Security numbers, birthdates, addresses - and in some instances, driver's license numbers - stolen by attackers. The company says that based on its investigation, it was hacked in mid-May, and attackers continued to access the data until the breach was discovered in late July.
In addition, Equifax says 209,000 U.S. consumers' credit card data was exposed in the breach, as were 182,000 U.S. consumers' "dispute documents," containing personal information. Equifax says it "also identified unauthorized access to limited personal information for certain U.K. and Canadian residents" and that it will "will work with U.K. and Canadian regulators to determine appropriate next steps."
The scale of the Equifax breach means that every SSN in the United States - together with the accompanying name - must be presumed to be public knowledge, and thus should not be used to validate anyone's identity, ever again, security experts warn.
"What this shows is that using SSNs, etc., as proof of online ID is useless. You now have to assume your personal data is out there," Alan Woodward, a professor of computer science at Surrey University, tells Information Security Media Group via Twitter.
2. Share SSN to See If We Lost It
Equifax, however, doesn't appear to have gotten that message.
The company has created a dedicated breach-notification website for U.S. victims, www.equifaxsecurity2017.com, as well as a dedicated call center.
"In addition to the website, Equifax will send direct mail notices to consumers whose credit card numbers or dispute documents with personal identifying information were impacted," the company says. "Equifax also is in the process of contacting U.S. state and federal regulators and has sent written notifications to all U.S. state attorneys general, which includes Equifax contact information for regulator inquiries."
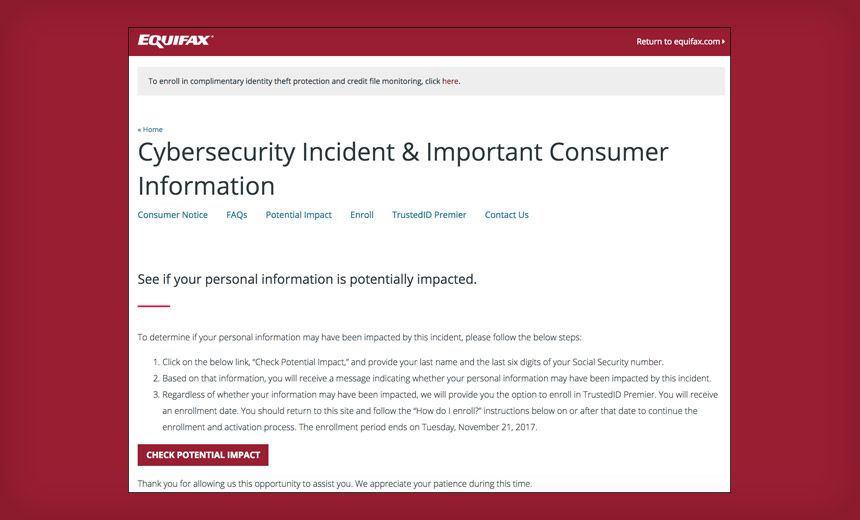
But on that website, which offers Cybersecurity Incident & Important Consumer Information, consumers who want to see if they've been impacted by the breach are told to "provide your last name and the last six digits of your Social Security number."
Many potential breach victims have criticized Equifax for requiring potential breach victims - whose SSNs may have been exposed - to validate their identity using their SSN.
"Asking for the last six digits of your SSN is a rocky start to the credit monitoring process," says Chris Pierson, the CSO and general counsel for financial technology payment firm Viewpost. "You have a population which just lost trust in the company. ... Hardly a way to rebuild trust and goodwill."
Instead, he says, the firm should have looked for other ways to validate breach victims.
"To ask for SSNs as opposed to name, date of birth and address show a misunderstanding of customer expectations," Pierson says. "In weighing speed to notify versus a functional credit monitoring solution, more time should have been taken to carefully plot out the remediation steps."
3. Notification Page Flagged as Malicious
Equifax's breach notification site itself also go off to a rocky start, according to England-based security researcher Kevin Beaumont, who notes that the page is being flagged as a phishing site by some security tools, which will block users from visiting it.
The phishing flag isn't a surprise, since the site was registered using a "free, shared CloudFlare SSL cert," says Facebook developer Daniel Lo Nigro via Twitter.
"There's no way to tell that it's a legit site. Could easily be a phishing site. This should be using an EV cert," he says, referring to an Extended Validation Certificate, used for HTTPS websites, to prove that the legal entity controlling the website or software package is who they claim to be.
One takeaway for other firms, Beaumont says, is that they should ensure that they register - and obtain an EV cert - in advance for any domain name they might want to use, to alert breach victims.
4. Marketing Funnel?
Equifax says all U.S. consumers - affected by the breach or not - can sign up to its "TrustedID Premier," which includes Experian, TransUnion and Equifax credit reports, which consumers can already obtain for free, every 12 months.
TrustedID Premier does, however, include "internet scanning for Social Security numbers" that Equifax has lost.
Equifax says it will offer TrustedID for free for 12 months, after which consumers must pay for it. Data breach expert Troy Hunt told ISMG that this apparent use of the breach as a marketing funnel shows "very poor judgment."
Meanwhile, based on an attempt to subscribe to the service on Sept. 8 by Information Security Media Group, enrollment is not instantaneous. Rather, the site said enrollment could only be completed by returning to the site on Sept. 14, via a specified link. "Please be sure to mark your calendar as you will not receive additional reminders," the site says.
5. Legalese: Customers Cannot Sue
TrustedID user, beware: Under "TrustedID Terms of Service," updated Wednesday, the day before Equifax's breach notification - customers of Equifax's TrustedID service must agree to terms and conditions that preclude them from ever suing Equifax.
Equifax didn't respond to a Friday query about whether the company would attempt to use that arbitration requirement to prevent breach victims from participating in any potential class-action lawsuits based on breaches that occurred before they signed up for TrustedID. But Schneiderman's office reported late Friday that it received assurances that Equifax will not attempt to use the clause to prevent breach victims from suing. Equifax also updated its breach FAQ to say that "the arbitration clause and class action waiver" does not apply to "the cybersecurity incident."
6. What Security Defenses Were in Place?
As noted, Equifax says attackers exploited a "website application vulnerability," which provides almost no technical detail.
Based on security experts' reviews of Equifax's website, however, it appears to rely on an extensive mix of older technology.
"Equifax's infrastructure is a weird mix of IBM WebSphere, Apache Struts, Java," Beaumont says via Twitter (see Apache Struts 2 Under Zero-Day Attack, Update Now). "It's like stepping back in time a decade."
So far, it's unclear if attackers exploited a known vulnerability in software used by Equifax or a zero-day flaw. But at least historically speaking, attackers who breach websites tend to do so using known flaws that have not yet been patched.
From a hygiene standpoint, on Friday, the security researcher known as x0rz reported finding at least one flaw that Equifax had failed to patch - a cross-site scripting, or XSS, vulnerability that the company was first warned about last year.
In terms of stealing data from Equifax, however, attackers wouldn't have used XSS. Instead, a remote-code exploitation attack, or exploiting a flaw that allowed an attacker to inject arbitrary SQL code into the website and dump databases, are most likely, x0rz says.
If attackers exploited an unpatched flaw, there's no excuse, Viewpost's Pierson says. "This all comes back to sound security development coding practices, active application scanning and testing, and integrating security into the engineering and development processes to make web applications more resilient," he says. "Really, it is the back to the basics of mitigating the OWASP Top 10 and SANS Top 20 vulnerabilities in your web application and make security the job of every engineer backed by a robust security and infrastructure team."
On a potentially related note, Experian until recently was seeking someone to fill the role of vice president of cybersecurity, to "manage the Cyber Threat Center, Security Operations, Security Architectures and Strategies, and Security Planning and Advisement functions," and report to the company's global CSO/CISO, who is in charge of physical and logical security.
7. Equifax Apologizes
To Equifax's credit, its CEO and chairman, Richard F. Smith, has issued a mea culpa, apologizing for the breach and promising to do better. "I've told our entire team that our goal can't be simply to fix the problem and move on," he says in a statement. "Confronting cybersecurity risks is a daily fight. While we've made significant investments in data security, we recognize we must do more. And we will."
Rick Smith, chairman and CEO of Equifax.To Equifax's credit, its CEO and chairman, Richard F. Smith, has issued a mea culpa, apologizing for the breach and promising to do better. "I've told our entire team that our goal can't be simply to fix the problem and move on," he says in a statement. "Confronting cybersecurity risks is a daily fight. While we've made significant investments in data security, we recognize we must do more. And we will."
8. Insider Trading Questions
Equifax's CEO can expect to be in the hot seat over how the company failed to prevent such a massive breach.
But the company is also facing potential insider trading questions following news reports that three executives sold stock worth about $1.8 million after the breach was discovered on July 29, before the company issued a public breach notification on Sept. 7 (see Data Breach Notifications: What's Optimal Timing? ).
As first reported by Bloomberg News, three Equifax executives sold stock in the company on August 1 and August 2, just days after Equifax discovered the breach.
The stock sales generated $946,374 for CFO John Gamble, $584,099 for U.S. Information Solutions President Joseph Loughran - who also exercised an option to purchase 3,000 shares at a price of $33.60 - and $250,458 for Consumer Information Solutions President Rodolfo Ploder earned, according to Marketwatch.
After Equifax's Thursday breach notification, the value of the company's stock fell 14 percent to $123 per share, according to Bloomberg analyst Anna Massoglia.
Equifax couldn't be immediately reached for comment on the stock sales. As Marketwatch has reported, "Most executives set up what is referred to as a 10b5-1 plan to sell shares on regular schedules, in order to avoid accusations of insider trading," and such plans are typically detailed on SEC filings. None of the Equifax executives' SEC filings, however, said that their stock sales were prescheduled.
But Ines Gutzmer, head of corporate communications for Equifax, told the Guardian: "The three executives who sold a small percentage of their Equifax shares on Tuesday, Aug. 1, and Wednesday, Aug. 2, had no knowledge that an intrusion had occurred at the time they sold their shares."
***
Update (Sept. 11): Noted that Equifax has now promised to not apply the arbitration clause to try and block lawsuits based on this breach.
